Networks in Action
Using WEP Security on an AirPort Network
Introduction
You and your wireless network get along very well. It moves files where you need them, checks Internet weather when asked, and says nice things about your friends and relatives. It’s your metaphorical family dog that runs on electricity. This dog is friendly, though. Very friendly. Did you know that anyone near your house, even across the street, can call and ask your dog to fetch stuff for them? If not, it’s time for network obedience school.
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP) is a way to protect network data moving from the AirPort Base Station (or ad hoc connection) to your computers. Using a specially generated software “key,” it scrambles the data. You need the key to unlock the data, so even if someone is listening in, it’ll look like garbage. WEP doesn’t keep them from receiving the wireless signal (nothing can, outside of shielding your walls and windows), but the data is useless without the key.
Someone Wrote It; It Must Be True
Many know WEP only by rumors of its design flaws. No lie—it’s not the world’s best security mechanism. However, it’s still practical for the standard home or small office user. Consider that the people you’re protecting against will steer clear of networks with any kind of security. Why break in through an upstairs window when the next house’s door is open? Just enabling WEP is most of the battle. Change the network key every week for even more security.
WEP and AirPort
Wireless products must support 64-bit WEP to be certified Wi-Fi compliant. There is also 128-bit WEP, but this article sticks to 64-bit, which all AirPort models support. Wi-Fi compliance shows as a logo on the box or Internet product description.

Assuming your network is already running, open the AirPort Admin Utility from the Utilities folder of your Applications directory. You should see your Base Station. If you don’t, verify that the Base Station’s power is on, then push Rescan.
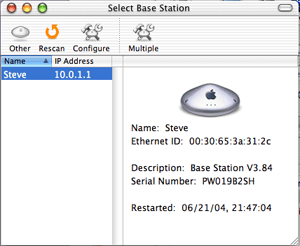
Double-click the AirPort name (Steve in my example) or select Configure to open the preferences window. This shows the summary page, which includes WEP details when they’re enabled. For now, it should say “not configured.”
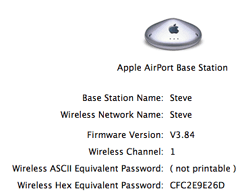
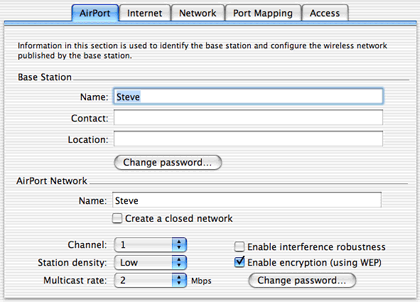
To enable WEP, select the Name and Password tab, then check Enable Encryption. Select Change Password… to open a window where you enter the new password twice. Then select Update to save the changes. Once the Base Station restarts, select it from the AirPort menu. If it asks for the password, enter it and save it to the keychain. Now the summary screen shows your Wireless Hex Equivalent Password.
Other Macs should do likewise—select the AirPort from the menu and enter the password to join. The password should be saved in the keychain, so you only need enter it once. Change this password any time you like using the same steps, or from the Show All Settings page.
Connecting a Windows 2000 system to my AirPort network required entering the Wireless Hex Equivalent Password, so you may need to write this down and carry it to the other computers. Macs should be able to use the password instead. (Your AirPort uses the password to generate the hex sequence, so the same password always generates the same hex values.)
Change your password weekly on home networks and more often on ones that see heavy use. This prevents snoopers from sitting and listening to traffic long enough to break the encryption scheme (very few will attempt this). Each new password renders any previous snooping useless.
Summary
WEP is a snap to enable, and its mere presence defends you from the majority of drive-by wireless thieves. Don’t let this security tool just sit in the box—protect your data before someone makes you wish you had.
Also in This Series
- Mac to Windows: Troubleshooting the “No Logon Servers Available” File Sharing Error · October 2004
- Using WEP Security on an AirPort Network · July 2004
- Whatever happened to…Threemacs.com? · September 2003
- Clandestine Wireless Networking and MacStumbler · July 2003
- Learning to Share With Others: Sharing Preferences Overview · April 2003
- Serving Files Using FTP in Mac OS X · December 2002
- Switching Between Networks in Mac OS X · November 2002
- The Audio/Video Quadras (660av, 840av) · September 2002
- Thoughts on Apple’s Xserve · July 2002
- Complete Archive
Reader Comments (8)
That said, WEP is definitely at least an order of magnitude more difficult to implement than it needs to be....
Overview of WEP packets, (I'm locked I'm locked I'm locked I'm locked I'm locked I'm locked I'm locked here's the key) :()
Add A Comment