Software Review
Espionage 2.0.2

Developer: Tao Effect
Price: $25; $5 (upgrade from 1.x)
Requirements: Mac OS X 10.5. Universal.
Trial: Fully-featured (14 days)
“I have nothing to hide.” I wish that were true. I don’t run a Ponzi scheme, so I don’t have to worry about hiding the list of places where my investors’ money really goes. Still, just by using Address Book, I have data like names and e-mail addresses that I prefer to keep away from prying eyes. Having separate accounts on a Mac, with separate passwords, is no defense against unwanted data access. Anyone with physical access to a Mac, with a moderate level of technical know-how, can access the data on the Mac’s hard disk. If you really need to safeguard the data you have on your hard disk, you need passwords and encryption, something that Tao Effect’s Espionage offers. Unlike Apple’s FileVault, Espionage can protect individual folders rather than your entire home folder, thus resulting in better performance.
Usage
The first time you launch Espionage, you will be prompted to set up a master password for use with the application. The password can be your login password or a different, new password. To protect a folder, you drag and drop the folder onto Espionage’s window and set a password. The next time you try to access the folder, you will be prompted to supply the password.
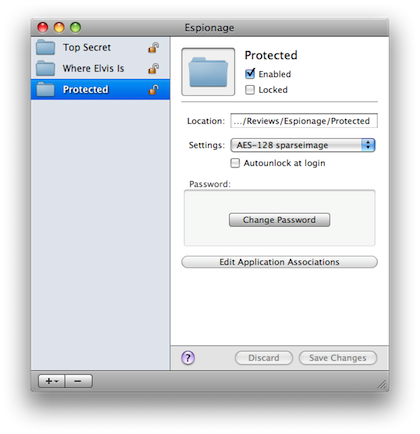
The Espionage interface.
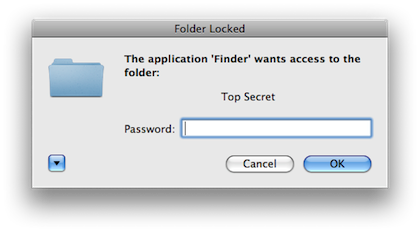
You need a password to see the folder’s content.
You can choose to only password protect the folder or to also encrypt the folder’s content. Espionage stores folders using Mac OS X disk images in one of two formats: .sparesbundle (more efficient for Time Machine) or .sparseimage (can save space for smaller folders). Encryption options are AES-128 or AES-256, which are government approved for Top Secret documents.
New with version 2.0 is Application Association. All users know where their movies, music, and pictures are, but many probably don’t know where to locate files related to Mail, iChat, etc. Espionage comes with an application template whereby you choose the application and Espionage looks up the path to the data associated with the application. In my example, I told Espionage to protect the data associated with the multi-protocol chat client Adium. If your application is not in the template, you do have to somehow identify its data location and drag the folder into Espionage. Once set up, when launched, the application will ask for the password. When you exit the application, its data is locked again.
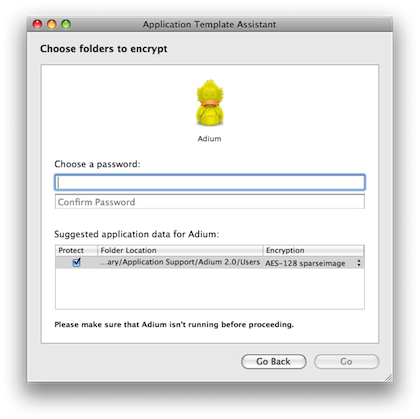
Espionage knows where Adium’s data is.
Even if someone boots my computer up from a system DVD and uses the password reset tool to make up a new admin password, my protected folder is still off-limits to the intruder. Likewise, if someone boots the computer in target disk mode and hooks a FireWire cable to it, while he can roam about the entire hard drive unobstructed, he does not really see the content of the protected folders. Instead, he is greeted by three “folders” whose names present the message:
This folder contains encrypted data. It is controlled by Espionage. Do not modify it in this state.
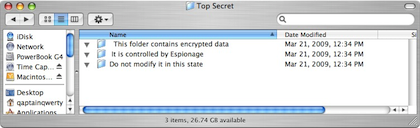
Even in Target Disk Mode, the folder is protected.
Under the Hood
Espionage works by replacing a folder that it protects with a hidden image file. Yes, Espionage actually deletes the folder and put in its place a different version of the original folder. Working with the kernel extension iSpy, Espionage listens for events requesting folder access and interferes with the request by presenting a password prompt. Espionage’s help shows you how to exclude certain processes from iSpy so that they do not generate password prompts. When the password check is passed, Espionage mounts the disk image file, also invisibly. If you have something important to protect, use a password and encryption.
When you first set up Apple’s FileVault, it sternly warns you that if you ever forget your password, no one in the world can help you. Espionage does not have such warnings, but I suppose it is the same deal. Be sure to use passwords that you’ve used elsewhere or that you won’t forget; do not choose something hard to remember. Before you have Espionage protect your data, it would be a good idea to back it up and to put the backup physically far from the production data.
Is It Transparent?
Tao Effect touts Espionage as intuitive, simple to use, and unobtrusive. While I agree with the first two claims, I have to disagree with the third one. So far, we know that once a folder is locked, trying to open it via the Finder and you will be prompted for the password. In reality, even when I was nowhere near the protected folder, just switching to the Finder triggered password prompts—yes, one prompt for every protected folder. I ended up unprotecting all the test folders. It seems any interaction between applications and the Finder makes Espionage think the protected folders are to be accessed. It is possible to add the Finder to Espionage’s whitelist, but then when you really want to go into the protected folders, you are no longer prompted for the password but instead are informed that the folder is protected by Espionage and so on. To access the folders, you would have to select the folders within Espionage and uncheck the Locked box.
Another example of quirky Finder integration is the Lock contextual menu. While you can select an unlocked folder and re-lock it this way, subsequent attempts at going into the re-locked folder would result with the error message:
The folder “folder_name” could not be opened because you do not have sufficient access privileges.
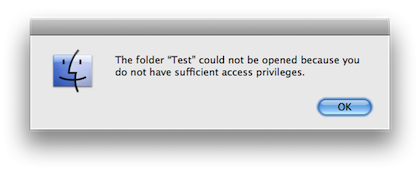
Instead of being prompted for the password, you are denied access instantly when folder is re-locked via the contextual menu.
Again, to unlock the re-locked folder, you would have to launch Espionage, select the re-locked folder, and uncheck its Locked checkbox. Tao Effect is aware of this issue and invites users to send in their system configurations.
Recall that folders protected by Espionage, when in use, are really mounted disk images. That means they are on the same level as other mounted volumes, like the hard drive. One of my favorite Finder shortcuts is to go to up a folder level by holding down the Command key and clicking the folder name. The entire folder structure leading up to the current folder is presented, and I can traverse it quickly. But with Espionage’s use of disk images, there is no folder structure to traverse. I still can use the back button, but it does not always correspond to a level up.
Just because Espionage allows having passwords for every folder that it protects does not mean you should use the feature. Eventually, the many passwords would become unwieldy. You may end up having to group folders that need to be protected under one folder. You now trade the freedom to keep separate folders in exchange for Espionage’s protection. Perhaps in a future release Espionage will allow unlocking all the folders once one of them is unprotected. Likewise, when setting up folders for protection, it would be convenient if there were an option to use an existing password by clicking some checkbox. All these examples translate to an obtrusive presence Espionage has on the protected computer.
While the process of protecting folders and unlocking them is intuitive, making use of the built-in backup feature is not. Introduced in version 2, the backup feature makes Espionage look worse. You tell Espionage which protected folder to backup via the Preferences panel. In my case, I told Espionage to use my Time Capsule to store the backups. The backups of protected folders appear in the backup location in the folder called EspionageBackups. An extra folder level is introduced to keep folders by the same name separated. The backups are already encrypted so that instead of the folder content, you see the now familiar message indicating that the folder are protected.
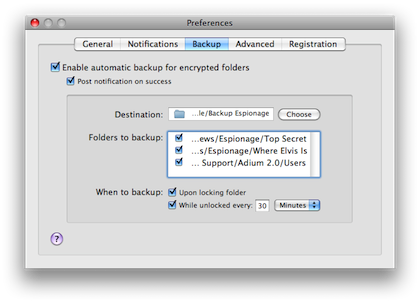
Backup is set up in Espionage’s Preferences panel, not in Tools of the main menu.
I can live with the strange placement of the backup function, but finding how to restore backed up folders got me totally confused. I looked for a button or menu option that would spell Restore but none was to be found. Instead, to restore a folder, you would copy it via Finder, in its protected state, back to where the original folder was, or any other place. You would drag the newly copied folder back into Espionage’s window and apply the same security settings. The folder, supposedly already encrypted before, would now be encrypted again. Open it with the correct password, and the folder is back where it should be. I think the more straightforward way to restore a folder from backup would be to select a menu option under Tools.
Summary
If you have sensitive data on your computer, Espionage provides a good solution to protecting the data. Someone with physical access to your computer has to overcome Espionage’s password protection and encryption to get to your data. Protected application data works fine, but the Finder interaction is not transparent. In my experience, Espionage prompted for the passwords for each protected folder at times when I was nowhere close to such folders. You can open up Espionage and lock or unlock folders within Espionage, but then you lose the transparency. The newly added built-in backup feature works fine in backup mode, but restoring folders involves a rather quirky process. Espionage gets the job done as far as encrypting and protecting folders, but it is obtrusive and not totally intuitive in the backup area, so for me it is only a Good product.
Reader Comments (4)
When a folder is locked via the contextual menu, only some macs, and only some of the time, will that strange error message appear from the Finder. The problem appears to be an odd caching issue with the Finder, where it will simply assume the folder is inaccessible and will not even attempt to access it. It's easily fixable by moving the folder slightly or getting info on it. Most users don't experience this issue at all. A system-wide menu for locking and unlocking folders is coming very soon, which will make it even easier to avoid this Finder/Espionage bug.
If you get the password prompt randomly claiming that the Finder is trying to access the folder, check to make sure that none of Finder windows are set to "Calculate all folder sizes" in the view options.
We also have plans to make it even easier to restore backups (very similar to the suggestions in this review), we did not include them in 2.0 initially because it would have delayed the release of 2.0, and restoring a folder is a rare operation, and the documentation makes it very clear on how to do so. We do agree though that this is a user-friendliness defect in the program, and it will be fixed in a free update soon.
We just released version 2.0.4, which adds new features (including support for custom folder icons), and addresses a couple of the issues brought up in this review, including the Finder's "insufficient privileges" prompt, and probably most (if not all) of the situations that could cause the password prompt to appear randomly. Hopefully now we can really live up to the unobtrusive claim. :-)
Full changes can be found here.
Add A Comment